
Intellexa’s Predator spyware can hide iOS recording indicators while secretly streaming camera and microphone feeds to its operators.
The malware does not exploit any iOS vulnerability but leverages previously obtained kernel-level access to hijack system indicators that would otherwise expose its surveillance operation.
Apple introduced recording indicators on the status bar in iOS 14 to alert users when the camera or microphone is in use, displaying a green or an orange dot, respectively.
US-sanctioned surveillance firm Intellexa developed the Predator commercial spyware and delivered it in attacks that exploited Apple and Chrome zero-day flaws and through 0-click infection mechanisms.
While its ability to suppress camera and microphone activity indicators is well known, it was unclear how the mechanism worked.

Source: Jamf
How Predator hides recording
Researchers at mobile device management company Jamf analyzed Predator samples and documented the process of hiding the privacy-related indicators.
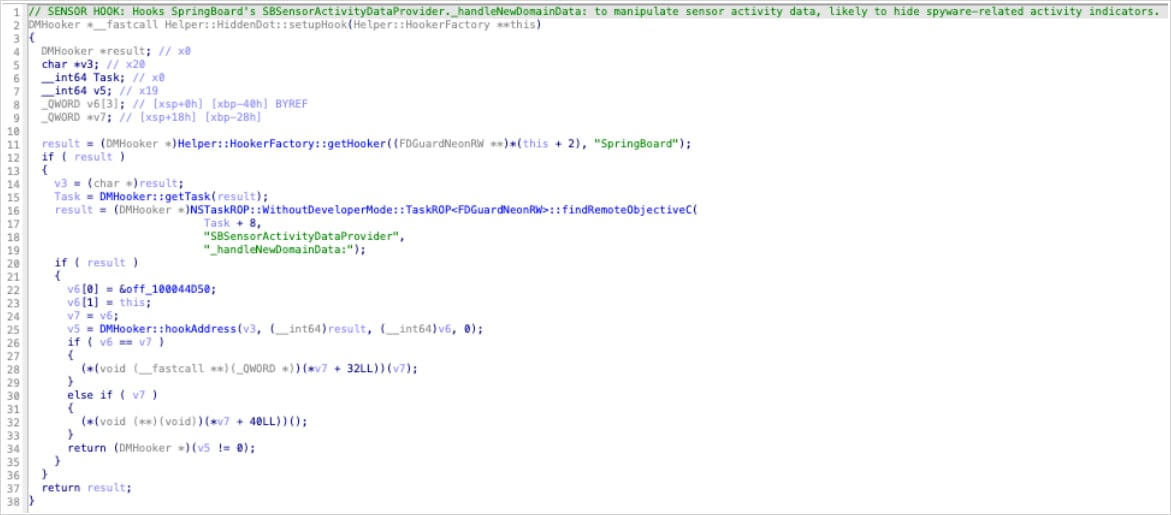
According to Jamf, Predator hides all recording indicators on iOS 14 by using a single hook function (‘HiddenDot::setupHook()’) inside SpringBoard, invoking the method whenever sensor activity changes (upon camera or microphone activation).
By intercepting it, Predator prevents sensor activity updates from ever reaching the UI layer, so the green or red dot never lights up.
“The target method _handleNewDomainData: is called by iOS whenever sensor activity changes – camera turns on, microphone activates, etc.,” Jamf researchers explain.
“By hooking this single method, Predator intercepts ALL sensor status updates before they reach the indicator display system.”
Source: Jamf
The hook works by nullifying the object responsible for sensor updates (SBSensorActivityDataProvider in SpringBoard). In Objective-C, calls to a null object are silently ignored, so SpringBoard never processes the camera or microphone activation, and no indicator appears.
Because SBSensorActivityDataProvider aggregates all sensor activity, this single hook disables both the camera and the microphone indicators.
The researchers also found “dead code” that attempted to hook ‘SBRecordingIndicatorManager’ directly. However, it doesn’t execute, and is likely an earlier development path that was abandoned in favor of the better approach that intercepts sensor data upstream.
In the case of VoIP recordings, which Predator also supports, the module responsible lacks an indicator-suppression mechanism, so it relies on the HiddenDot function for stealth.
Jamf further explains that camera access is enabled through a separate module that locates internal camera functions using ARM64 instruction pattern matching and Pointer Authentication Code (PAC) redirection to bypass camera permission checks.
Without indicators lighting up on the status bar, the spyware activity remains completely hidden to the regular user.
Jamf notes that technical analysis reveals the signs of the malicious processes, such as unexpected memory mappings or exception ports in SpringBoard and mediaserverd, breakpoint-based hooks, and audio files written by mediaserverd to unusual paths.
BleepingComputer has contacted Apple with a request for a comment on Jamf’s findings, but the company never responded.


