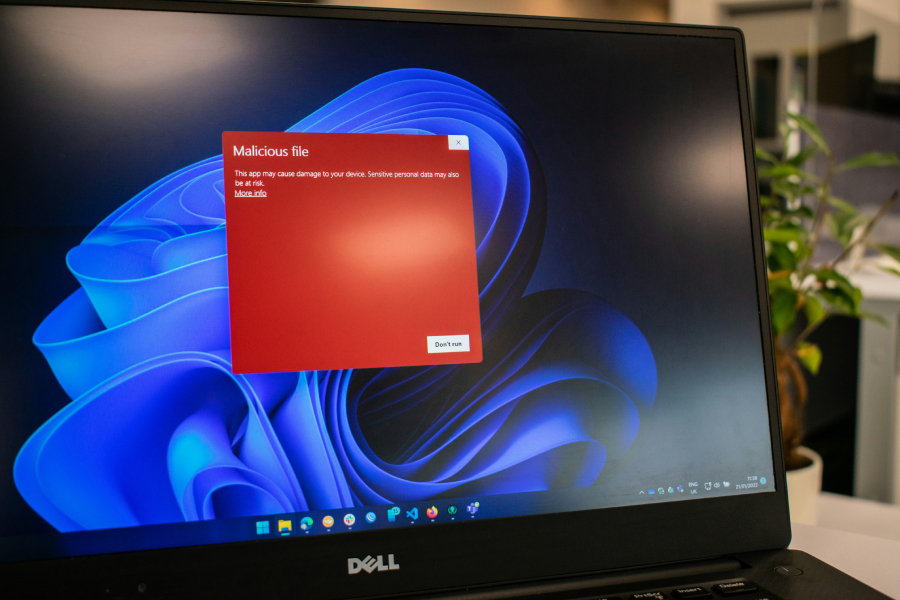
A new social engineering campaign is abusing fake CAPTCHA verification pages to trick Windows users into launching StealC information-stealing malware.
The attack relies on compromised websites that display convincing Cloudflare-style security checks, prompting victims to manually execute malicious PowerShell commands under the guise of routine verification.
“StealC exfiltrates browser credentials, cryptocurrency wallets, Steam accounts, Outlook credentials, system information, and screenshots to a command-and-control (C2) server using RC4-encrypted HTTP traffic,” LevelBlue researchers said.
Inside the StealC infection chain
StealC harvests browser credentials, email logins, cryptocurrency wallet data, and system information, enabling account takeover, fraud, and lateral movement. These risks are amplified by a multi-stage, largely in-memory infection chain that complicates detection and forensic analysis.
The attack begins when a user visits an otherwise legitimate website that has been compromised by threat actors. Malicious JavaScript embedded in the site loads a fake CAPTCHA page that closely mimics Cloudflare’s verification interface. Instead of presenting a visual challenge, the page instructs the user to press Windows Key + R, then Ctrl + V, and finally Enter, claiming these steps are necessary to complete the verification process.
This approach, referred to as ClickFix, exploits the fact that users rarely question simple keyboard instructions when they believe they are interacting with a trusted security control.
In practice, a malicious PowerShell command is already placed on the clipboard and executes when pasted into the Run dialog, giving the attacker code execution without triggering browser download prompts or security warnings.
After execution, the PowerShell script connects to a remote server to retrieve position-independent shellcode generated using the Donut framework. The shellcode is reflectively loaded into memory and used to launch a custom 64-bit PE downloader compiled with Microsoft Visual C++.
The downloader retrieves the final StealC payload and injects it into svchost.exe, a legitimate Windows service process that blends into normal system activity. Once resident, StealC communicates with its command-and-control infrastructure over HTTP, encrypting traffic using a combination of Base64 encoding and RC4 encryption.
Dual-layer string obfuscation further conceals critical configuration data, including C2 server addresses, targeted file paths, and database queries. Active campaigns targeted browser credentials, cryptocurrency wallets, Steam authentication data, Outlook email accounts, and system screenshots.
How organizations can reduce risk
Addressing fileless, socially engineered attacks requires greater emphasis on behavior and access patterns rather than traditional malware artifacts.
Because these campaigns rely on built-in system tools and user interaction, effective detection depends on monitoring process activity and access to sensitive data.
- Monitor for fileless attack behavior, including encoded PowerShell commands, shellcode injection patterns (VirtualAlloc/CreateThread), and suspicious process injection into svchost.exe.
- Alert on anomalous access to browser credential stores, cryptocurrency wallet artifacts, and unexpected clipboard-to-execution activity originating from browsers.
- Restrict interactive script execution by hardening PowerShell usage, limiting the use of abuse-prone utilities, and enforcing enhanced logging and AMSI visibility.
- Apply application control policies (for example, WDAC or AppLocker) to block unauthorized scripts, reflective loaders, and unsigned binaries.
- Monitor outbound network traffic for unusual User-Agent strings, suspicious domains, and command-and-control patterns tied to browser-initiated processes.
- Reduce endpoint credential exposure by limiting browser password storage, isolating privileged accounts, and separating sensitive wallets or admin access from daily browsing.
- Regularly test incident response plans and tabletop exercises for fileless malware attack scenarios.
Collectively, these steps help organizations reduce risk and build resilience.
Editor’s note: This article originally appeared on our sister website, eSecurityPlanet.