Risk has many dimensions, and different stakeholders have different threat models and risk appetites. Cybersecurity risk is no exception. For example, a vulnerability in a software library could be critical to your operations if you are using the component of the library in which the vulnerability resides, but barely relevant if you are not. The Stakeholder-Specific Vulnerability Categorization (SSVC) methodology is a framework for different stakeholders to prioritize vulnerabilities according to their distinct risk appetites. Unlike other vulnerability categorization systems that rate on technical severity (impact on operations should the vulnerability to be exploited) or exploitability (how likely it is that there will be an exploit), SSVC rates vulnerabilities based on risk to the concerned stakeholder. It is not a one-size-fits-all solution. The approach enables stakeholders to effectively prioritize and guide vulnerability responses, even when some data is missing. In this blog post, we highlight recent updates to SSVC, including:
- new tooling for onboarding to SSVC
- improved documentation that is more accessible and robust
- modernized software development practices
- integration with other vulnerability management standards
In December 2019, the CERT Coordination Center (CERT/CC) developed and released SSVC as an open-source and transparent project so interested adopters can understand the thought process and methodology behind design decisions. Since then, it has gained adoption by enterprises of varying sizes, including NTT DATA and Yahoo. Furthermore, CISA is operationalizing SSVC at scale, which drives continued feedback and improvements to SSVC. Adopters can select from preconfigured decision models, presented as decision tables, and either use them as-is or customize them. SSVC also supports building decision models from the ground up using a methodical, critical approach that reflects the specific risk appetite of a stakeholder.
The community of SSVC users is still growing, and that means there are more likely to be users who need the capability to be more approachable and easier to implement in their environments. Supporting a broader audience requires tools and better documentation that are more digestible. Furthermore, SSVC adoption has reached the point where folks want it to be available in other standardized data feeds like the Common Vulnerabilities and Exposures (CVE) and Common Security Advisory Framework (CSAF) formats.
Recent Updates in SSVC for 2025
Navigating SSVC Made Easy: Meet the SSVC Explorer and the Upgraded SSVC Calculator
SSVC Explorer
The new SSVC Explorer project provides an interactive view into decision tables that the SSVC community developed. Using the SSVC Explorer’s user-friendly, point-and-click interface, analysts can navigate well-designed decision models, modify existing decision tables, or create new models by leveraging SSVC community-developed ones or self-authored (customized) decision points. The SSVC Explorer is a comprehensive tool for users to explore the creation of decision points and decision tables.
SSVC Calculator
The upgraded SSVC Calculator allows vulnerability analysts to use a readily available decision table to evaluate a vulnerability. Alternatively, analysts can customize their own decision table. The interactive calculator allows for ad-hoc or orderly evaluation of a vulnerability using either publicly available information or a specific understanding of the vulnerability and its impact to the user’s environment.
The SSVC Knowledge Hub: Guides and Documentation
Based on community feedback, we enhanced SSVC documentation to make the framework more accessible to everyone. The new SSVC Overview guide replaces the previous tutorial pages and is designed for nontechnical security practitioners, or anyone new to SSVC. The guide introduces the framework; explains how stakeholders are defined; and walks through how to create decision points, develop decision tables, and evaluate vulnerabilities using SSVC. For those entirely unfamiliar with SSVC, the SSVC Overview guide is the ideal starting point.
Decision Tables
What was once referred to as a decision tree or decision policy is now represented as a decision table—a clear, structured way to map decision points to outcomes and produce a vulnerability category. Figure 1, below, illustrates an example decision table generated by the SSVC Explorer tool, that was described earlier in this blog.
In the years since we initially released SSVC, our understanding has evolved. As part of that evolution, we recognize that our initial choice to represent SSVC decision models as decision trees has both advantages and disadvantages. On the plus side, SSVC novices find the tree representation to be intuitive and easy to understand. On the minus side, folks more familiar with machine learning-based decision trees are sometimes confused because we were using a definition of the term that is incongruous with the canonical definition of decision tree in the machine learning domain. While searching for a new term, we landed on decision table, which is much closer to the concept we originally intended to describe with SSVC decision models.
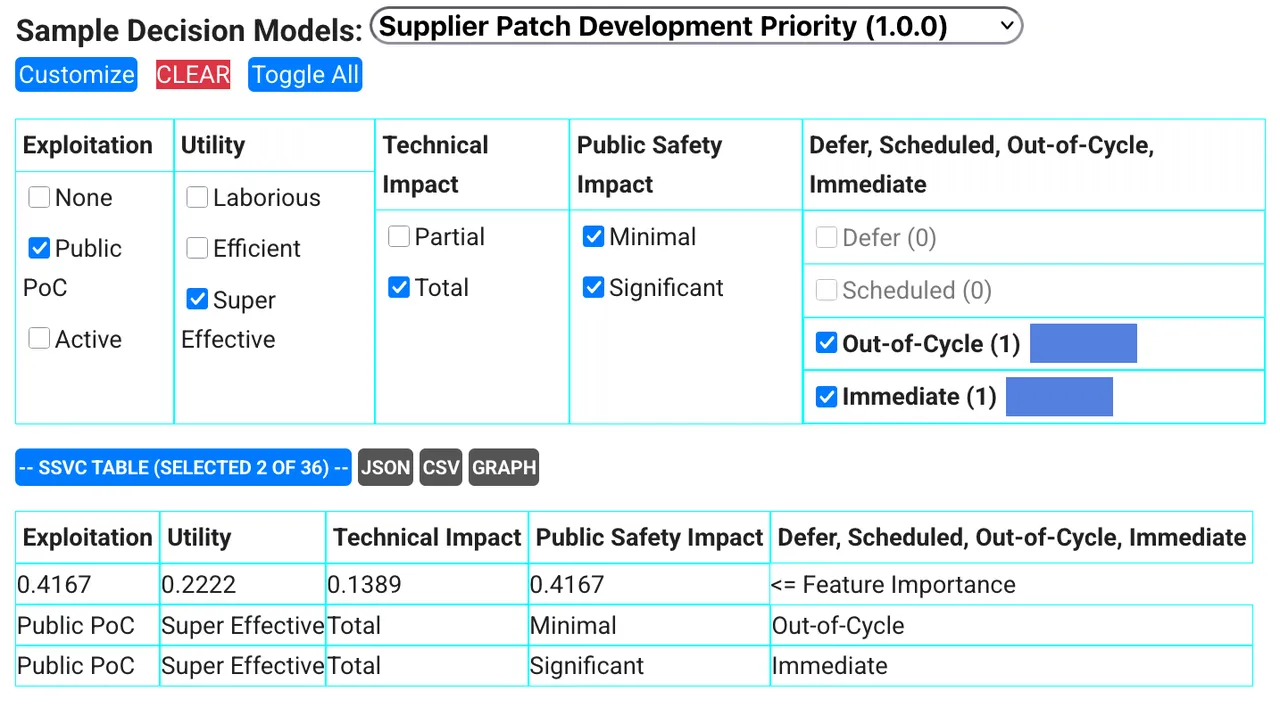
Figure 1: Options to toggle to render a Supplier Patch Development Priority Decision Table
Functionally speaking, nothing about SSVC decision models changes. A decision table can be represented as a decision tree (using the operations research definition). Our hope in making this change is that, over time, it will become clearer how SSVC decision models are constructed. Users that are more comfortable with the decision tree framing can continue working with trees, as depicted below in Figure 2.
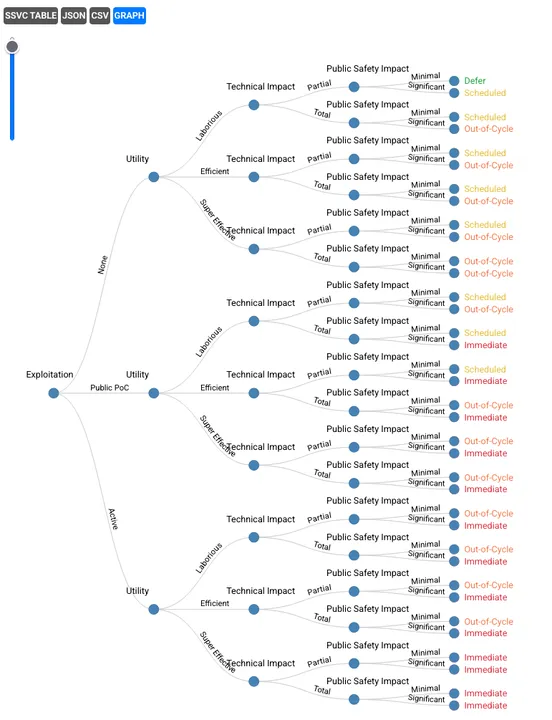
Figure 2 The full decision tree for Supplier Patch Development Priority
Decision Points
SSVC’s decision points have been refined and tested in operational settings to ensure that they can be clear, distinct, and easily communicated by analysts. By integrating ongoing research in vulnerability management, we can offer guidance to help analysts more confidently navigate the complex task of vulnerability prioritization. The decision point guidance also helps SSVC newcomers create decision points that are precise and reproducible, thus reducing overlap and ambiguity and making them easier to defend and consistently apply across different scenarios.
A New SSVC Toolbox – Frameworks, Software, and Containers
Our software is built with Python because Python has become the de facto language for modern automation, data analysis, and machine learning. Python’s readability, extensive ecosystem of libraries, and active community make it ideal for rapidly developing, scaling, and integrating automation workflows. It also aligns well with educational use and reproducible research, which makes it a strong fit for both industry and academic users.
We modernized our coding practices to embrace contemporary Python software patterns spanning
- API frameworks like FastAPI; scientific libraries including SciPy, NumPy, and scikit-learn
- data-modeling tools Pydantic and JSON Schema
- pytest for a testing framework
- containerization with Docker for streamlined deployment and integration
All of these components are published in the CERT/CC GitHub project and on the certcc-ssvc PyPI package, making them easy to install, integrate, and directly test in your environment. This approach enables teams to systematically and cost-effectively adopt proven, modern techniques, without needing specialized consultants or costly bespoke development work.
These tools also assist in creating versioned Python objects for decision points and decision tables, enhancing transparency so that adopters can explore or revert to earlier versions at any time. The framework supports namespace-based decision points and tables, including experimental namespaces that enable safe mock testing for events such as hackathons and tabletop exercises, fostering collaboration and innovation without impacting production workflows.
Bridging Frameworks: How SSVC Adapts the CVSS and EPSS Scoring Systems and Integrates with CSAF and CVE Reporting Formats
SSVC does not exist in a vacuum—it builds on and contributes to the broader ecosystem of vulnerability management standards. CVSS vector elements and SSVC decision points share a common pattern in one sense: CVSS vectors can be directly represented as SSVC decision points, and as a whole, CVSS V4 can map into an SSVC decision table. This mapping provides flexibility for consumers to include CVSS vectors, if preferred, into an SSVC decision table without having to learn or develop new decision points. Likewise, scoring systems, such as EPSS, that focus on exploitation can also be incorporated to reflect a decision maker’s comfort with quantitative exploitability “predictive” measures inside the SSVC framework.
Again, SSVC is designed for transparency and traceability. SSVC JSON templates, with their structured definitions, naturally integrate with machine-readable vulnerability reporting formats, such as the Common Security Advisory Framework (CSAF). Moreover, the CVE record format, with its API-based services, provides another ideal channel for publishing SSVC metrics that are time-tracked, publicly accessible, and easy to consume. By embedding SSVC metrics into CVE records and CSAF reports, we can communicate, in a standardized and machine-readable format, the careful, timely evaluations that analysts perform when evaluating vulnerabilities.
Work with Us to Shape the Future of SSVC
This release introduces a range of new capabilities designed to help users refine their understanding of SSVC and explore new ideas for implementation. CISA’s sponsorship of SSVC since its inception in 2019 has provided us crucial support and feedback for this important element of vulnerability coordination. Nonetheless, SSVC remains a work in progress, and its success depends on your engagement and adoption. We ask the community to provide feedback—including how you are using SSVC at your organization—and help us make SSVC even more useful for cybersecurity practitioners. Join the conversation on our GitHub page to help further this project onwards and upwards.

